
9to5Mac Safety Chew is completely delivered to you by Mosyle, the one Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in method to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Technology EDR, AI-powered Zero Belief, and unique Privilege Administration with probably the most highly effective and trendy Apple MDM in the marketplace. The result’s a completely automated Apple Unified Platform at the moment trusted by over 45,000 organizations to make thousands and thousands of Apple gadgets work-ready with no effort and at an inexpensive price. Request your EXTENDED TRIAL at this time and perceive why Mosyle is all the things you want to work with Apple.
Safety researchers have recognized an try by state-sponsored hackers from North Korea (DPRK) to focus on Mac customers with infostealer malware via a trojanized assembly app.
As soon as contaminated, the malware would set up a connection between the Mac and the attacker’s command and management (C2) server to exfiltrate delicate information like iCloud Keychain credentials. It was additionally discovered to quietly set up the distant desktop software AnyDesk and keylogging software program within the background to take over machines and accumulate keystrokes.
The malware, a brand new variant of a recognized pressure dubbed “BeaverTail,” was first reported by MalwareHunterTeam through a publish on X. Whereas BeaverTail was an current JavaScript data stealer found in 2023, it now seems to have been reworked to focus on Mac customers with a malicious disk picture titled “MicroTalk.dmg.”
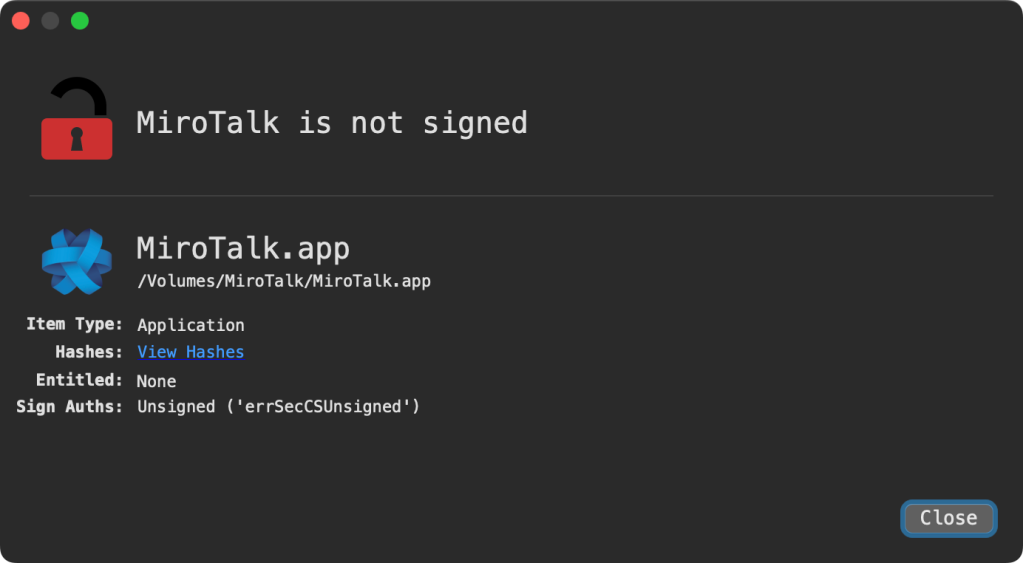
Safety researcher and writer Patrick Wardle analyzed the malware in a reasonably complete and hilariously titled weblog publish on Goal-See. Wardle discovered that hackers have been almost definitely posing as job recruiters, tricking victims into downloading what gave the impression to be the official video conferencing platform MiroTalk, hints the “MicroTalk.dmg” disk picture file identify, however was really a clone containing hidden malware.
About Safety Chew: Safety Chew is a weekly security-focused column on 9to5Mac. Each week,Arin Waichulis delivers insights on information privateness, uncovers vulnerabilities, and sheds mild on rising threats inside Apple’s huge ecosystem of over 2 billion energetic gadgets.

This wouldn’t be the primary report of North Korean hackers posed as job recruiters to focus on victims. Palo Alto Community’s notorious Unit42 analysis group lately reported on an analogous story titled: “Hacking Employers and Looking for Employment: Two Job-Associated Campaigns Bear Hallmarks of North Korean Risk Actors.”
In accordance with Wardle’s evaluation, the malicous MicroTalk clone containing the malware is unsigned or hasn’t been registered with Apple by an recognized developer, so macOS Gatekeeper will forestall the applying from executing. Nonetheless, customers can circumvent the block by right-clicking and hitting “Open” from the shortcut menu.

Gatekeeper is a daily headache for cybercriminals focusing on Mac customers. The truth is, it’s turn into such an efficient nuisance that in some circumstances, they instruct the consumer to open the malicious software the “Right” method (aka right-clicking and hitting “Open”) as a substitute of double-clicking.
As soon as contaminated, the malware communicates with C2 servers to obtain and extract information, together with iCould KeyChain credentials and browser extension IDs of in style cryptocurrency wallets, which can be utilized to steal non-public keys and mnemonic phrases. What’s most elusive, nonetheless, is when the malware was found final week, it might go via antivirus scanners, like VirusTotal, utterly undetected. Cybercriminals will add their executables on platforms like VirusTotal to make sure the malicious elements are hidden nicely sufficient to stay undetected from in style scanners. The draw back is the “good guys” can see them too.
“Particularly from the image’s output, we see strategies names (fileUpload, pDownFinished, run) that reveal doubtless exfiltration and obtain & execute capabilities,” based on Ojective-See’s weblog publish.
“And from embedded strings we see each the deal with of the doubtless command & management server, 95.164.17.24:1224 and likewise hints as to the kind of info the malware accumulate for exfiltration. Particularly browser extension IDs of in style crypto-currency wallets, paths to consumer browsers’ information, and the macOS keychain. Different strings are associated to the obtain and execution of further payloads which seem to malicious python scripts.”
On the finish of the day, I wouldn’t be stunned if that is the work of BlueNoroff, a subgroup of the nation-state’s well-known cybercrime enterprise, Lazarus Group. There have been a number of distinctive circumstances of BlueNoroff typically reaching out to potential victims beneath the disguise of an investor or firm head hunter. If it seems to be like a duck, swims like a duck, and quacks like a duck, then it most likely is a duck.
FTC: We use earnings incomes auto affiliate hyperlinks. Extra.


