
The infamous FIN7 hacking group has been noticed promoting its customized “AvNeutralizer” device, used to evade detection by killing enterprise endpoint safety software program on company networks.
FIN7 is believed to be a Russian hacking group that has been energetic since 2013, initially specializing in monetary fraud by hacking organizations and stealing debit and bank cards.
They later moved into the ransomware house and have been linked with the DarkSide and BlackMatter ransomware-as-a-operation platforms. The identical risk actors are additionally probably tied to the BlackCat ransomware operation, which just lately performed an exit rip-off after stealing a UnitedHealth ransom fee.
FIN7 is thought for classy phishing and engineering assaults to realize preliminary entry to company networks, together with impersonating BestBuy to ship malicious USB keys and growing customized malware and instruments.
So as to add to the exploits, they created a faux safety firm named Bastion Safe to rent pentesters and builders for ransomware assaults with out the candidates figuring out how their work was getting used.
FIN7 hackers are additionally tracked underneath different names, together with Sangria Tempest, Carbon Spider, and the Carbanak Group.
FIN7 promoting instruments to different hackers
In a brand new report by SentinelOne, researchers say that one of many customized instruments created by FIN7 is “AvNeutralizer” (aka AuKill), a device used to kill safety software program that was first noticed in assaults by the BlackBasta ransomware operation in 2022.
As BlackBasta was the one ransomware operation utilizing the device on the time, the researchers believed that there was a connection between the 2 teams.
Nevertheless, SentinelOne’s historic telemetry has proven that the device was utilized in assaults by 5 different ransomware operations, displaying a large distribution of the device.
“Since early 2023, our telemetry information reveals quite a few intrusions involving varied variations of AvNeutralizer,” explains a report by SentinelOne researcher Antonio Cocomazzi.
“About 10 of those are attributed to human-operated ransomware intrusions that deployed well-known RaaS payloads together with AvosLocker, MedusaLocker, BlackCat, Trigona and LockBit.”
Additional analysis revealed that risk actors working underneath the aliases “goodsoft”, “lefroggy”, “killerAV” and “Stupor” had been promoting an “AV Killer” on Russian-speaking hacking boards since 2022 for costs starting from $4,000 to $15,000.
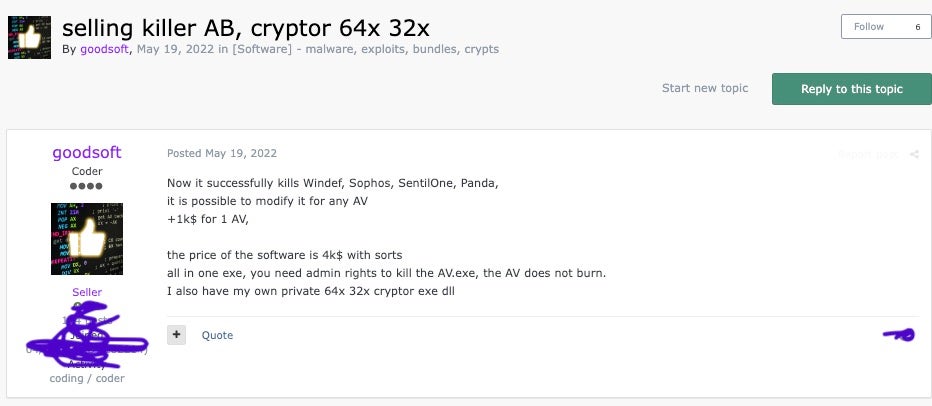
Supply: SentinelOne
A 2023 report from Sophos detailed how AvNeutralizer/AuKill abused the authentic SysInternals Course of Explorer driver to terminate antivirus processes working on a tool.
The risk actors claimed that this device could possibly be used to kill any antivirus/EDR software program, together with Home windows Defender and merchandise from Sophos, SentinelOne, Panda, Elastic, and Symantec.
SentinelOne now discovered that FIN7 have up to date AVNeutralizer to make the most of the Home windows ProcLaunchMon.sys driver to hold processes, making them now not operate appropriately.
“AvNeutralizer makes use of a mixture of drivers and operations to create a failure in some particular implementations of protected processes, finally resulting in a denial of service situation,” explains SentinelOne.
“It employs the TTD monitor driver ProcLaunchMon.sys, obtainable on default system installations within the system drivers listing, along side up to date variations of the method explorer driver with model 17.02 (17d9200843fe0eb224644a61f0d1982fac54d844), which has been hardened for cross course of operations abuse and is at present not blocked by the Microsoft’s WDAC listing.”
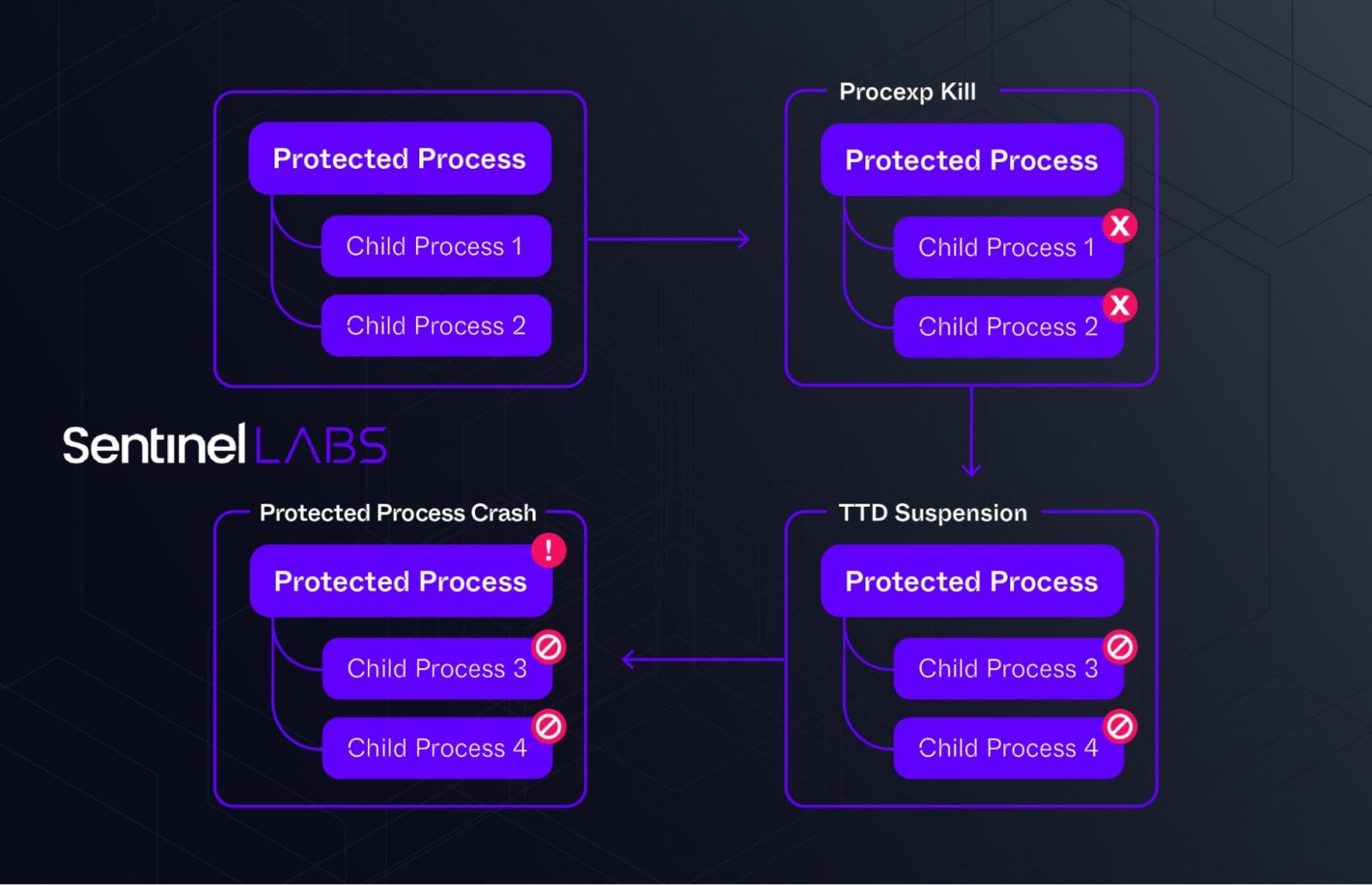
Supply: SentinelOne
SentinelOne discovered extra customized tooling and malware utilized by FIN7, which isn’t recognized to be bought to different risk actors:
Powertrash (a PowerShell backdoor), Diceloader (a lightweight C2-contolled backdoor), Core Impression (a penetration testing toolkit), and a SSH-based backdoor.
The researchers warn that FIN7’s continued evolution and innovation in tooling and strategies, in addition to the promoting of its software program, make it a big risk to enterprises worldwide.
“FIN7’s steady innovation, significantly in its subtle strategies for evading safety measures, showcases its technical experience,” concludes SentinelOne researcher Antonio Cocomazzi.
“The group’s use of a number of pseudonyms and collaboration with different cybercriminal entities makes attribution tougher and demonstrates its superior operational methods.”


